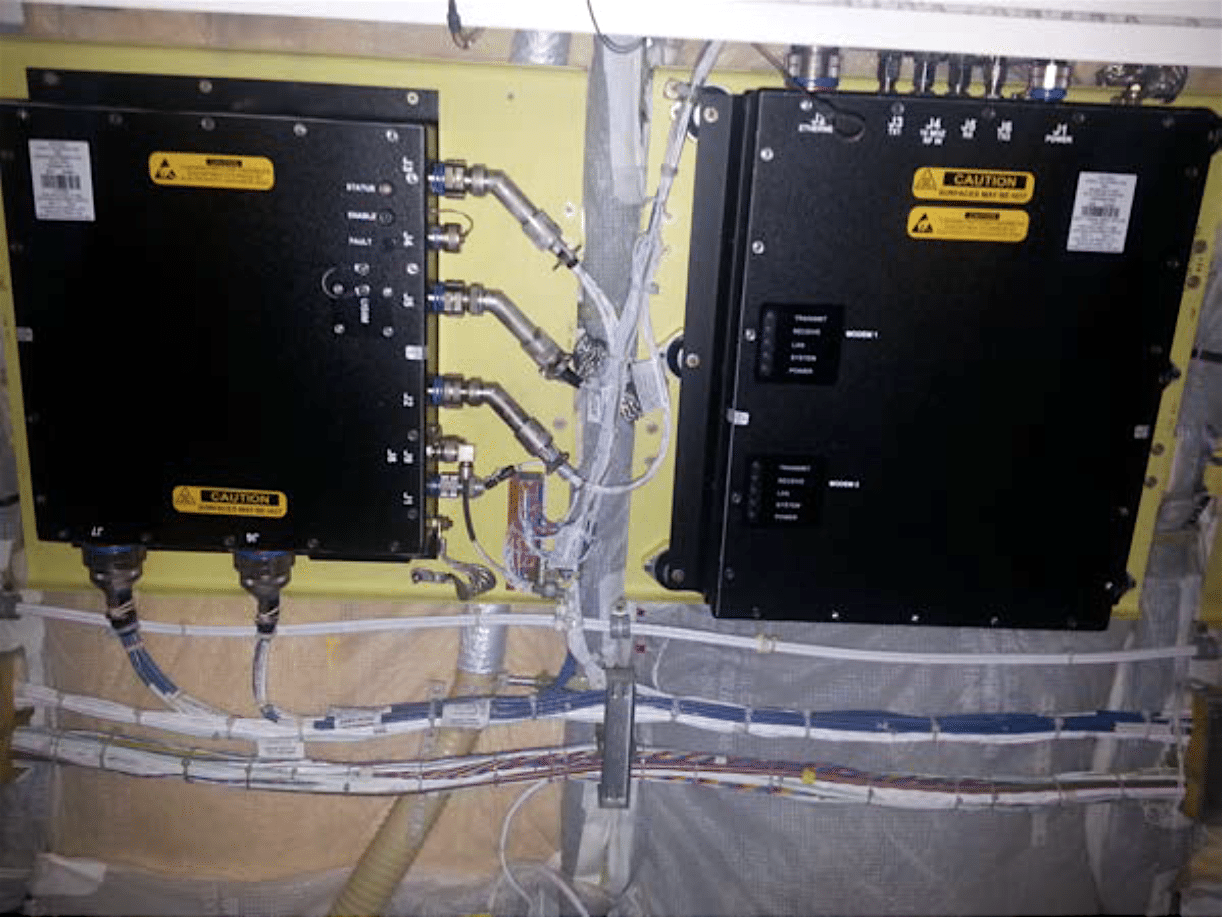
An airplane server management unit (left) serves as the system controller, providing core functionalities to the airplane modem (right) and high-power transceiver, as well as passengers and flight crews. (IOActive)
Cybersecurity consultant Ruben Santamarta used a “backdoor” vulnerability to demonstrate his ability to hack into a commercial airplane’s satellite internet modem. The vulnerabilities did not put safety-critical avionics systems at risk and have since been resolved by vendors.
A member of security firm IOActive, Santamarta presented his findings at the recent Blackhat security conference in Las Vegas. IOActive published a 70-page report detailing the findings of Santamarta and Josep Pi Rodriguez—also a security consultant for the company—that demonstrate their ability to establish a presence on an in-flight commercial aircraft.
“The main entry point that was exposed to the internet was the airplane modem data unit (MDU),” Santamarta told Avionics. “The satellite modem or router was the entry point, but the problem is, once you compromise that device, it is possible to jump to other devices. A compromised satellite modem gives you access to other devices connected to the same network segment.”
Santamarta said he first started looking into the scenario more intensely in November 2017 during a Norwegian Airlines flight from Madrid to Copenhagen. The aircraft featured free internet access to passengers, provided by internet connectivity equipment supplied by Kontron, Tecom and Row44, a subsidiary of Global Eagle Entertainment. The equipment is also featured on hundreds of aircraft operated by Air China, AirFrance and Icelandair, among others.
On the Norwegian flight, Santamarta used a free open-source computer network-monitoring tool called Wireshark to access internet traffic that originated at the airplane’s in-flight Wi-Fi access point. He noticed that the internet protocol (IP) addresses assigned to passenger mobile devices using the in-flight Wi-Fi appeared to be routable. According to Santamarta, a routable IP uses an internet communications protocol that contains an IP device and network address, which allows its network communication packets to be forwarded from one network to another. Most modern internet connected devices use protocols that only contain the device’s IP address.
When the flight landed, a network scan showed that a web interface unit could be accessed without authentication, which is shown in the image below. That gave Santamarta access to the airplane’s modem where a variety of attacks can be performed.

“Once you have control over the modem it is possible to perform additional attacks against passenger devices,” said Santamarta, noting that he could use the access to the modem to connect passenger mobile devices with malicious websites or software updates.
Santamarta also shows in the report how he gained access to an actual in-flight airplane internet satellite modem manufactured by Hughes. He previously highlighted theoretical attacks on Hughes satellite communications terminals in 2014, especially noting vulnerable backdoors.
Companies embed backdoors in their products usually as part of a “design pattern,” according to Santamarta. By reading the HX200—the product model of the airplane modem that was breached—Santamarta was able to discover software that is capable of installing new firmware on the modem itself. A Google search gave him the ability to download the “fallback updater software” used by the modem.
The following images from the IOActive report show a step by step process of how Santamarta was able to “reverse engineer” the binary associated with the firmware used to provide software updates for the modem.
1. Discovering software that is a good candidate for hosting “backdoor” access.

Santamarta’s description of how he discovered where “backdoor” access to the airplane’s modem could be hosted. Software developers use “backdoors” to give un-authenticated access to a device.
2. Discover the login prompt for the updating mechanism.

3. Access the password prompt from the modem’s update file server.

4. Establish a “shell” presence on the airplane’s modem.

Additionally, the connection to the satellite terminal would give a hacker the possibility to attack satellite infrastructure. The terminals are controlled remotely by Network Operations Centers operated by providers of satellite communications networks. Access to the NOC allows control and the ability to remotely configure terminal to attack the satellite infrastructure.
“That’s a theoretical possibility. We haven’t tried that but we have performed that attack in other scenarios and so we know it is possible,” said Santamarta.
The report capturing Santamarta’s research also includes numerical analysis of radio-frequency (RF) hazards attributed to vulnerable satellite communications devices. The devices could theoretically be exploited to target aircraft with a cyber-physical attack where a hacker could take control of the steering mechanism for an airplane antenna.
“We verified this was possible in other systems such as those used in the maritime industry, but we discovered that in the aviation sector it wasn’t possible,” said Santamarta.
A unique aspect of Santamarta’s research was that it was largely aided by information acquired from publicly available documentation of airplane satellite internet connectivity equipment configurations, such as press releases, YouTube videos, news articles and patents. The main aircraft equipment that Santamarta focused on included the modem data unit, antenna control unit, server management unit, satellite antenna assembly and high power transceiver featured in an ARINC 791 airplane satellite internet equipage design package. By accessing the modem, he could jump to the other above mentioned devices and compromise their functionality as well.
Rodriguez, a colleague of Santamarta at IOActive, presented research related to Santamarta’s modem hacking threat vector demonstration at the 2018 Defcon conference in Las Vegas recently. Rodriguez’s research shows the vulnerability of the Wing operating system (WingOS), which is an operating system widely used for aircraft wireless access points and wireless controllers. Millions of such devices use WingOS, including those supplied by Motorola, Zebra and ExtremeNetworks.
When an attacker exploits devices using the WingOS security flaw, they can then jump to other devices of the internal network that are not normally reachable from the internet. Since the attacker now has code execution at the WingOS device, now the attacker can pivot and try to attack these other assets inside the internal network, Rodriguez said.
“ExtremeNetworks fixed the risk in OS, the vendors have fixed or upgraded the OS it should be fixed. There are possible considerations to mitigate vulnerabilities found in WingOS for the aircraft, we’ve been talking with some vendors for the aircraft industry to make sure their configurations were not vulnerable,” said Rodriguez.
Santamarta also concluded his report noting that IOActive reported issues discovered to EASA, EU and U.S. certification authorities as well as the affected vendors. The company also worked with Aviation Information Sharing Analysis Center (ISAC) which provided feedback and information about how airlines are using the equipment he focused on.
“We can confirm that the affected airlines are no longer exposing their fleets to the Internet,” the report concludes.